

Authorities businesses, with their advanced networks and huge knowledge shops, have at all times confronted ongoing cybersecurity challenges that require subtle options. As they proceed to embrace digital transformation at their services, safety has by no means been extra vital. With extra belongings and processes on-line, businesses should implement new methods to maintain them secure.
Key takeaways
- Cybersecurity is a shared duty throughout all departments in authorities businesses, not simply the IT division
- The connection between bodily and cybersecurity is essential, requiring built-in safety methods
- Leveraging knowledge from office programs will help set up baselines to detect potential safety breaches
- When deciding on a facility administration answer supplier, contemplate their monitor file, cybersecurity experience, and knowledge privateness insurance policies
A part of the reply stays tried-and-true strategies, together with organizational vigilance and worker training. The digitization of office and facility administration, although, means there are actually extra knowledge units businesses can leverage to strengthen total safety.
The rising significance of cybersecurity for presidency businesses
In 2024, the variety of politically motivated cyberattacks towards U.S. federal entities surged, with 117 authorities organizations reporting ransomware incidents, up from 95 in 2023, in line with Statista.
On the municipal degree, 60% of state and native governments reported experiencing a cyberattack previously 12 months, and 45% of municipalities acknowledged service interruptions because of these incidents
The precise numbers are seemingly greater. The Statista report notes, “As with different sectors it’s vital to acknowledge that it seemingly represents solely a portion of the particular affect. Many ransomware assaults go unreported for causes corresponding to issues about nationwide safety and the need to keep away from disrupting essential providers.”
When it comes to monetary affect, the common value of an information breach for a authorities entity reached $9.5 million in 2024.
Frequent misconceptions about cybersecurity
Improved security begins with clearly defining cybersecurity.
One of many extra frequent misconceptions is that cybersecurity is the unique duty of the IT division. Whereas the IT division performs a essential function, they will’t do all of it. Cybersecurity is a shared duty, and each division throughout the enterprise is concerned. In reality, each worker has a task to play in defending the corporate.
For instance, workers want to concentrate on the most recent cybersecurity threats and tips on how to shield themselves from them. Additionally they have to be cautious about what info they share on-line about themselves and the corporate.
One other frequent misunderstanding is that cybersecurity is a one-time funding.
Cybersecurity is an ongoing course of as a result of the panorama is consistently altering, so businesses have to consistently replace safety measures to remain forward of the curve by implementing software program patches, updating safety insurance policies, and coaching workers on the most recent threats.
Understanding the connections between bodily and cybersecurity
One of many largest misconceptions is that cybersecurity is just about defending your community and knowledge. Whereas that’s a vital a part of the method, it’s just one piece of the puzzle.
Cybersecurity additionally includes defending:
- Folks
- Processes
- Bodily belongings
For instance, a cybercriminal may acquire entry to your community by a phishing assault, then use that entry to steal delicate knowledge, and even disrupt your operations. They might steal credentials on-line after which use them to realize bodily entry to your services. Or, working in reverse order, they’d break right into a facility for simpler entry to delicate materials by an onsite terminal.
For instance, when a metropolis’s water therapy facility is outfitted with sensors and management programs related by the Industrial Web of Issues (IIoT), a cyberattack may be simply as disruptive and harmful as somebody bodily tampering with the tools. A number of U.S. municipalities have reported tried breaches of water infrastructure programs, prompting federal alerts and emergency response coordination.
Or when a police division’s automobile fleet is supplied with GPS and distant entry programs, a hacker can compromise officer security or operational integrity simply as simply as a automobile thief as soon as may with a crowbar. In a 2024 incident, a ransomware assault on a county sheriff’s workplace disabled dispatch programs and automobile monitoring for over 48 hours, delaying emergency response instances.
These examples underscore the necessity for built-in safety methods that shield each digital and bodily belongings. For presidency businesses, this implies aligning cybersecurity protocols with facility entry controls, surveillance programs, and emergency preparedness plans to make sure continuity of public providers.
How you can strengthen cybersecurity: Customary greatest practices
With the rise of subtle cyberattacks, it’s important to take proactive measures to guard delicate knowledge and infrastructure, together with:
- Implement multi-factor authentication (MFA): MFA provides an additional layer of safety to your group’s programs and knowledge. By requiring customers to supply a number of types of identification, corresponding to a password, a safety token, or a biometric identifier, MFA considerably reduces the danger of unauthorized entry to delicate info
- Educate workers: Educating your workers about frequent cyber threats, corresponding to phishing emails and social engineering strategies, helps them establish and report potential safety incidents. Conduct common coaching classes and consciousness campaigns to make sure workers perceive their function in sustaining the group’s safety
- Run safety audits: Frequently conducting complete safety audits is an important step in figuring out vulnerabilities and potential safety dangers inside your group. Audits assist organizations assess numerous facets of IT infrastructure. By figuring out vulnerabilities early on, you possibly can take the mandatory steps to mitigate dangers and forestall potential breaches
Collectively, these practices type a powerful basis for defending towards evolving threats. By staying vigilant and repeatedly enhancing cybersecurity protocols, authorities businesses can higher shield public knowledge and preserve uninterrupted entry to important providers.
How you can strengthen bodily safety: Customary greatest practices
As threats to authorities services turn out to be extra advanced, strengthening bodily safety is simply as essential as securing digital programs.
Businesses can take deliberate steps to safeguard buildings, belongings, and personnel by confirmed methods, together with:
- Implement entry management programs: Use cellular credentials, biometrics, and cloud-based platforms to regulate who enters your constructing. Combine customer administration instruments for real-time oversight and audit trails
- Monitor entrances and exits: Deploy sensible surveillance programs with AI-powered analytics, movement detection, and facial recognition. Guarantee protection of all key entry factors and integration with alarms and entry logs
- Handle customer entry: Digitize check-ins with QR codes, pre-registration, and automatic badge printing. Use watchlists and alert programs to flag potential dangers whereas sustaining compliance with privateness legal guidelines
- Run safety audits: Carry out scheduled critiques of programs and insurance policies, together with penetration testing and compliance checks. Use scenario-based drills to check readiness and establish gaps
These measures assist make sure that public sector services stay safe, resilient, and ready to answer each on a regular basis dangers and high-impact incidents. When paired with robust cybersecurity protocols, bodily safety performs a significant function in defending the continuity of presidency operations.
Why complete safety additionally leverages facility administration knowledge
Because the traces blur between bodily and cybersecurity, there are alternatives for facility managers to work with IT departments and third-party software program suppliers to extend safety.
Historically, organizations have arrange three distinct, siloed know-how architectures at a facility:
- Cybersecurity
- Bodily safety
- Facility administration
Cybersecurity structure can embrace workstations, firewalls, digital non-public networks (VPNs), and different safety home equipment. Bodily system structure consists of mixtures of cameras, badge readers, door sensors, and hearth detection and suppression programs.
A fashionable facility administration answer features a sturdy characteristic set, with programs for asset monitoring, desk and room reserving, customer administration, occupancy and utilization monitoring based mostly on sensors, area planning, and transfer administration. Added to those knowledge units are ones from IoT belongings and tools in addition to operational know-how (OT), {hardware} and software program that detects or causes modifications by immediately monitoring belongings, processes and occasions.
By capturing and analyzing knowledge out of your facility system, you possibly can set up baselines for particular actions. Robust deviations from these baselines could point out a safety breach that your staff can rapidly examine.
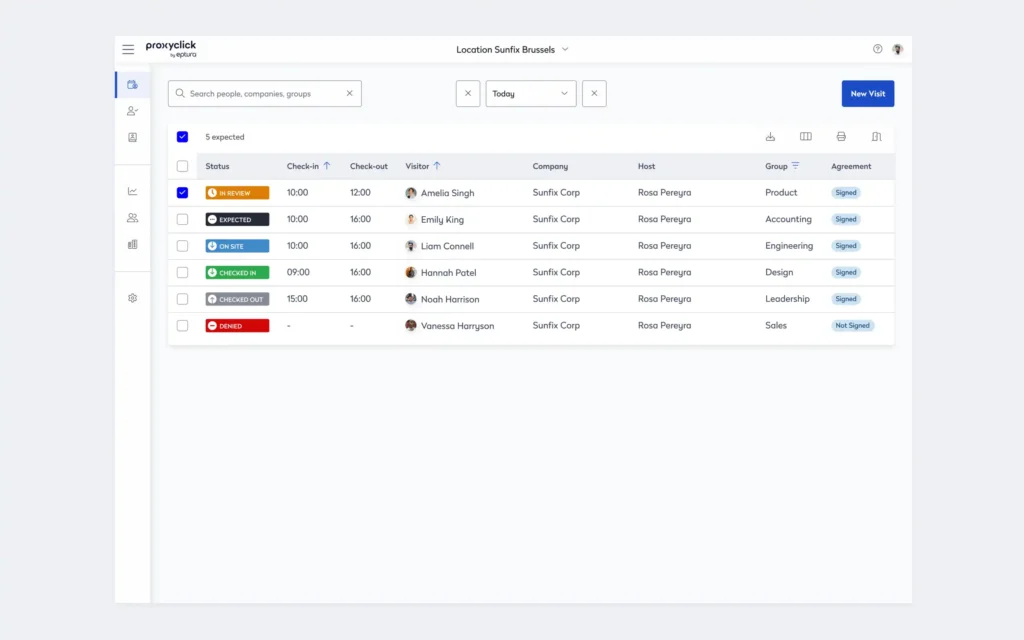

For instance, you possibly can create occupancy and utilization baselines utilizing knowledge from sensors, desk and room bookings, and customer administration programs. You may discover patterns like these in Eptura’s 2025 Office Index report, for instance a midweek spike in exercise, otherwise you may discover that your services behave in a different way from {industry} norms.
Digging deeper, you possibly can monitor tendencies at particular controlled-access doorways, particularly these resulting in server rooms or different delicate areas.
A contemporary facility administration system helps you identify baselines by offering solutions to fundamental questions on your services, together with:
- How usually do workers entry totally different areas in every constructing?
- Is entry extra frequent within the morning, afternoon, or after hours?
- Are sure days busier than others or is occupancy typically regular?
- How usually is entry denied and what are the most typical causes?
When you’ve established these baselines, you possibly can monitor for anomalies. A sudden enhance in entry throughout off-hours may sign covert exercise. A spike in entry denials may imply somebody is testing stolen credentials to seek out one which works.
How you can choose a facility administration answer supplier that may shield you and your knowledge
When deciding on a software program vendor, it’s important to conduct thorough analysis and contemplate a number of key components.
At the start, consider the seller’s monitor file in offering dependable and efficient safety options. Search for a vendor with a confirmed historical past of success within the cybersecurity {industry} and a powerful repute for delivering high quality services.
One other essential issue to contemplate is the seller’s cybersecurity experience. Assess their technical capabilities, certifications, and {industry} affiliations to make sure they possess the mandatory information and expertise to deal with the precise safety challenges giant enterprises encounter. Search for distributors that make use of skilled cybersecurity professionals and put money into steady analysis and growth to remain forward of threats.
Information privateness insurance policies and compliance with {industry} requirements are deciding components. Fastidiously evaluate the seller’s knowledge dealing with practices, privateness insurance policies, and safety measures to make sure they align together with your group’s knowledge safety necessities. Search for distributors which are clear about their knowledge utilization and cling to industry-recognized safety requirements.
The worth of FedRAMP
For U.S. authorities businesses, the FedRAMP market simplifies the method of discovering options.
“You really are constructing an info system for federal authorities use, and the federal government is authorizing that system to be used for federal knowledge,” explains James Masella, vp of compliance advisory providers at Coalfire, a supplier of IT safety assessments for a lot of safety requirements and funds frameworks and packages, together with FedRAMP assist.
After passing a rigorous safety audit, distributors are listed within the FedRAMP Market, the place federal businesses can simply discover and procure cloud providers. Whereas businesses should assess particular dangers, FedRAMP streamlines the method by offering a standardized, reusable safety framework.
In the long run, a proactive method to discovering cybersecurity companions is important for presidency businesses that want to guard belongings, preserve belief, and guarantee continuity within the face of evolving threats.
Join, community, and be taught at GSX with Eptura
Proper now, safety is prime of thoughts for a lot of, with specialists coming collectively for International Safety Trade (GSX) 2025, Sept. 29–Oct. 1.
The annual occasion consists of specialists from throughout the safety {industry} and options alternatives to earn CPE credit, discover the most recent applied sciences, and construct methods to remain resilient towards in the present day’s cyber and bodily threats.
Eptura is happy for the chance to current on the occasion and share insights from our Office Index report and recommendation from our {industry} specialists.
Securing the Good Buildings of 2025: Bridging Gaps in an Period of Convergence
Time and date: 9:45–10:45 a.m. Wednesday, Oct. 1
Presenters: Richard Noel, director of safety operations and infrastructure, Eptura, and Matt Fox, vp of product administration, Eptura
Key takeaways:
- Understanding the convergence of IT, OT, IoT, and bodily safety programs
- Methods for securing sensible buildings in advanced hybrid environments
- Instruments and applied sciences for enhancing safety, together with AI, analytics, and built-in platforms
- Bridging gaps between bodily and digital safety groups
As sensible buildings and related applied sciences reshape the way you handle your areas, the convergence of bodily safety with OT, IoT gadgets, and facility administration platforms introduces new layers of complexity. Whereas these improvements supply higher effectivity and perception, in addition they expose your group to evolving cyber-physical threats that demand a extra built-in and proactive method to safety.
The presentation will cowl probably the most urgent challenges going through safety professionals in 2025 and acquire sensible methods for shielding your belongings, folks, and knowledge. You’ll learn to establish rising dangers, reply to disruptions in interconnected environments, and use knowledge out of your programs to enhance decision-making and incident response.
Additionally be sure that to go to Eptura at Sales space 512 discover facility options constructed to assist smarter, extra environment friendly facility operations. The staff can be out there to elucidate product capabilities, focus on integration methods, and reply questions on how Eptura suits into safety packages.




