A single breach can cripple payroll. In an incident reported on Might 7, 2024, a serious cyber-attack compromised a third-party payroll system utilized by the UK’s Ministry of Defence, exposing the names and financial institution particulars of roughly 270,000 service members. The assault highlighted the numerous dangers inherent within the software program provide chain
IBM’s 2024 Price of a Knowledge Breach Report discovered that the typical value per document for stolen worker Personally Identifiable Data (PII) was $189. Nevertheless, this determine is a mean, and the true value can differ dramatically primarily based on business and geography, with the general common value of a breach reaching $4.88 million globally.
Payroll recordsdata pack salaries, Social Safety numbers, tax IDs, and financial institution accounts—knowledge the GDPR and California’s CPRA now guard with hefty fines for any lapse.
That’s why forward-looking HR and finance leaders are adopting payroll-data-protection software program. This information breaks down the seven security measures that matter and the seller questions that separate actual safeguards from advertising and marketing fluff. Let’s shield each paycheck collectively.
The 2025 risk–and-compliance backdrop
Hackers have realized that the quickest strategy to damage an organization is to strangle payroll. Provide-chain assaults, exemplified by the 2023 MOVEit breach, display the cascading danger of a single vulnerability. A flaw within the extensively used MOVEit file-transfer software program was exploited by the Cl0p ransomware group, exposing the information of over 93 million people throughout greater than 2,700 organizations, together with the UK payroll supplier Zellis. The incident, with estimated prices exceeding $10 billion, underscores that an organization’s safety is contingent on the integrity of its software program suppliers. Even a well-guarded enterprise is just as sturdy because the file-transfer software behind its pay run.
Regulators are elevating the stakes. GDPR fines can attain €20 million or 4 % of worldwide income, whichever is increased. California’s CPRA ended the long-standing HR-data exemption on January 1, 2023. This pivotal regulatory change prolonged the total suite of client privateness rights to California-based workers, candidates, and contractors. Consequently, these people now possess the proper to know what private data is collected about them, the proper to request the deletion of their knowledge, and the proper to right inaccurate data held by their employer. This enlargement of rights creates important new operational obligations for HR and payroll departments and mandates that payroll software program platforms present sturdy performance to handle and fulfill these knowledge topic requests. Greater than twenty U.S. states have now enacted their very own privateness legal guidelines, creating a fancy patchwork. Vanta’s GRC framework rolls the necessities of the 5 state legal guidelines already in pressure – CCPA/CPRA, CPA, CTDPA, UCPA and VCDPA – right into a single management set and automates proof assortment, so payroll groups can get audit-ready quicker.
Management feels the strain. Business evaluation signifies a rising concern amongst HR and payroll leaders relating to knowledge safety, pushed by growing regulatory strain and high-profile breaches. For instance, a current Sage report on South African companies discovered that knowledge safety was a major driver for cloud adoption, with 70% of respondents citing automated tax calculations and 56% citing centralized payroll and worker knowledge as key advantages of cloud methods. When these worries collide with fines and model harm, selecting safe payroll knowledge safety software program shifts from nice-to-have to non-negotiable.
With that context in place, let’s discover the seven capabilities that set really safe payroll platforms aside.
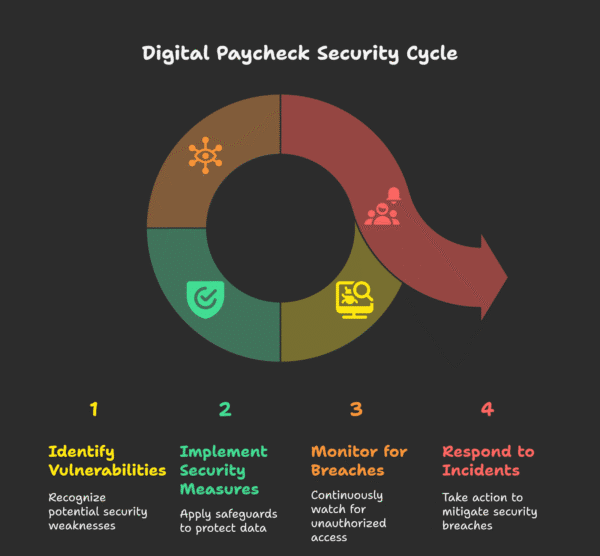
1. Lock down entry with role-based permissions
Insider abuse is a big risk. The Affiliation of Licensed Fraud Examiners (ACFE) 2024 Report back to the Nations discovered that asset misappropriation, which incorporates payroll fraud, is the commonest type of occupational fraud, occurring in 89% of instances. Whereas these schemes have the bottom median loss at $120,000, the length of fraud is a key issue; the everyday fraud case lasts for a median of 12 months earlier than detection. Moreover, the perpetrator’s stage of authority is strongly correlated with the scale of the loss, with frauds dedicated by house owners or executives leading to a median lack of $500,000, in comparison with $60,000 for workers. The longer it stays hidden, the extra salaries, Social Safety numbers, and financial institution accounts an attacker or a disgruntled worker can siphon off.
The treatment is the precept of least privilege. Efficient payroll-security software program helps you to outline granular roles (payroll supervisor, HR assistant, finance reviewer) so every individual sees precisely what they want and nothing extra. A junior assistant would possibly right mailing addresses however by no means view internet pay, whereas a finance reviewer can approve totals but can’t alter financial institution particulars.
Sturdy platforms reinforce these partitions with twin approval. Any try to vary a routing quantity or add a brand new payee triggers a second-person sign-off and an indelible timestamp within the audit log. If one thing does go improper, you’ll be able to retrace each step and know exactly who touched what.
While you demo an answer, ask the rep to create a “restricted HR temp” position on the spot. If the duty takes greater than a minute or they should name engineering, transfer on. In 2025, tightly managed permissions are the baseline for severe payroll safety.
2. Require multi-factor authentication each time
Passwords alone are brittle. The 2025 Verizon Knowledge Breach Investigations Report (DBIR) confirms that stolen credentials stay a dominant preliminary entry vector, implicated in 22% of confirmed breaches. When a single password is the one barrier to the payroll system, the complete group’s monetary integrity is in danger. Multi-factor authentication (MFA) is the important management to mitigate this danger. Nevertheless, it’s essential to acknowledge that not all MFA is created equal. Attackers are more and more using subtle strategies like Adversary-in-the-Center (AiTM) phishing and session token hijacking to bypass weaker, phishable types of MFA akin to SMS codes and easy push notifications. Subsequently, top-tier platforms should assist and implement trendy, phishing-resistant authentication components like FIDO2 safety keys to supply significant safety. When one username and password unlock a complete payroll vault, each paycheck rests on the weakest hyperlink.
Multi-factor authentication (MFA) fixes that flaw. By including a second proof—an authenticator-app code, a {hardware} key, or a fingerprint—you pressure criminals to steal two secrets and techniques without delay. Even when a phisher methods an worker out of a password, the break-in stalls on the second immediate. The additional step takes customers seconds but stops most credential-stuffing bots and social-engineering makes an attempt.
Good payroll-security software program makes MFA necessary. Admins can flip a single change that enforces it for everybody, from the CFO to a brief HR intern. High-tier platforms additionally assist trendy components akin to FIDO2 safety keys (far stronger than SMS codes) and weave MFA into single sign-on so workers see one clear gateway whereas IT retains management.
While you demo a system, ask two questions: Is MFA necessary, or merely accessible? and how briskly can we allow it for each account? If the reply includes plug-ins, work-arounds, or obscure roadmap guarantees, preserve purchasing. A second issue must be first-class citizenship in any platform that protects paychecks.
3. Encrypt knowledge in transit and at relaxation
Payroll data is foreign money in its purest kind: account numbers, salaries, and tax IDs. Leaving it unencrypted is like setting a briefcase of money on a park bench. Sturdy encryption shuts the locks, so even when thieves seize the briefcase, all they see is unreadable code.
Main payroll-security platforms apply 256-bit AES encryption the second a document hits disk and transfer each byte via a TLS 1.2 or increased tunnel. The keys stay inside a devoted {hardware} safety module, safely outdoors the database. That single design selection issues: Sturdy encryption is a foundational management for knowledge safety, mandated as an ‘acceptable technical measure’ underneath laws like GDPR Article 32. Whereas quantifying the precise ROI of encryption might be advanced, its worth is obvious: it renders stolen knowledge unreadable and ineffective to attackers. The absence of affordable safety controls like encryption can result in considerably elevated regulatory penalties within the occasion of a breach. Main payroll platforms should apply sturdy, standardized encryption, akin to 256-bit AES, to all knowledge at relaxation and make the most of safe transport protocols like TLS 1.2 or increased for all knowledge in transit. Verification of those controls via SOC 2 reviews or penetration check outcomes is a crucial due diligence step.
Regulators agree. GDPR Article 32 calls encryption an “acceptable technical measure,” and California’s CPRA will increase penalties when “affordable safety” akin to encryption is lacking. If knowledge leaks with out encryption, fines multiply.
One missed hole is how payslips journey. In case your supplier nonetheless emails plain PDFs, insist on a safe self-service portal or, at minimal, password-protected recordsdata. Throughout diligence, ask the seller to supply proof akin to pen-test reviews or SOC 2 controls that show encryption is all the time on. If these paperwork don’t seem shortly, transfer on; an open briefcase is rarely well worth the danger.
4. Monitor every little thing with audit trails, then let real-time alerts do the shouting
The IBM Price of a Knowledge Breach 2024 report reveals that the typical breach lifecycle is 258 days, comprising 194 days to determine the breach and an extra 64 days to comprise it. This prolonged ‘dwell time’ earlier than detection supplies a crucial window for attackers to function unnoticed. Shortening this lifecycle has a direct and important monetary impression; breaches contained in underneath 200 days value a mean of $3.84 million, whereas these lasting longer value $5.46 million—a distinction of over $1.6 million. Complete audit trails present the mandatory visibility, whereas trendy, real-time alerting and anomaly detection are the mechanisms that shrink the detection window and set off the speedy response wanted to mitigate monetary harm. Every login, wage change, or bulk export is time-stamped, user-stamped, and sealed in opposition to tampering. When regulators ask for proof of “acceptable accountability controls” underneath SOC 2 or GDPR Article 30, these logs communicate for you. SOC 2 compliance software program like Vanta robotically aggregates that proof throughout your methods, so producing an audit-ready report can drop from weeks to hours.
Cameras alone don’t cease crime; alarms do. Fashionable platforms layer real-time monitoring and AI-driven anomaly detection on high of the logs. If somebody tries to obtain the total payroll at 2 a.m., the system pings you, suspends the session, and preserves forensic proof in a single movement. That on the spot response shortens the breach life cycle and, in keeping with IBM, can save practically $1 million in cleanup prices.
Throughout a demo, filter the exercise log for “wage change,” then set an alert for any export bigger than final month’s complete. If the rep can’t full each steps in underneath two minutes, the platform shouldn’t be prepared to protect paychecks in 2025.
5. Demand speedy, computerized safety updates
Unpatched software program stays a major gateway for attackers. The 2025 Verizon DBIR highlights a big resurgence on this space, with the exploitation of vulnerabilities now serving because the preliminary entry vector in 20% of all breaches—a 34% year-over-year enhance. Occasions just like the MOVEit assault, which stemmed from a single unpatched vulnerability in a file-transfer software, show that delayed patching can have catastrophic, supply-chain-wide penalties. Subsequently, a vendor’s potential to ship speedy, computerized safety updates with out requiring shopper motion shouldn’t be a comfort however a crucial protection in opposition to a documented and rising risk vector. The 2023 MOVEit ransomware spree proved the purpose when payroll outsourcers that delayed a crucial replace noticed hundreds of thousands of worker data posted on leak websites.
Cloud-native payroll knowledge safety software program closes these gaps in hours, not weeks. Engineers push fixes throughout each tenant the identical day a vulnerability is disclosed, normally with no downtime and no motion out of your IT workforce. By morning, payroll clerks log in unaware that the system simply averted a pricey incident.
While you vet a vendor, press for specifics:
- How lengthy did you are taking to deploy your most up-to-date crucial patch?
- Do you publish launch notes that flag safety fixes?
- Is patching totally computerized, or should shoppers schedule upkeep home windows?
A assured rep will reply in hours or days, not quarters or obscure street maps. Something slower leaves the door open for attackers.
6. Insist on hermetic backups and catastrophe restoration
Payroll is a weekly heartbeat; miss one beat and the entire physique panics. Payroll is a time-critical enterprise perform the place any disruption has quick penalties. Whereas exact hourly downtime prices differ, the paramount significance of enterprise continuity is obvious. Within the present risk panorama, a sturdy backup and catastrophe restoration (BCDR) technique isn’t just about recovering from {hardware} failure; it’s a cornerstone of ransomware resilience. The 2025 Verizon DBIR reviews that ransomware was a part in 44% of all breaches. A technique constructed on immutable, off-site backups with clearly outlined and examined Restoration Level Aims (RPO) and Restoration Time Aims (RTO) is what permits a corporation to get well its operations with out capitulating to extortion calls for. The truth that 64% of ransomware victims now refuse to pay the ransom is a testomony to the rising effectiveness of such restoration capabilities. When that system is payroll, the oblique price ticket consists of offended employees, regulatory fines for late wages, and morale that takes months to restore.
Nice payroll knowledge safety software program plans for the worst earlier than it occurs. Search for platforms that replicate knowledge in close to actual time to a second area, shrinking your recovery-point goal to minutes. Simply as very important is the recovery-time goal: main distributors can spin up a contemporary surroundings and resume pay runs inside a couple of hours as a result of they rehearse full failovers a minimum of twice a yr and share the outcomes with clients.
Redundancy should lengthen past the first cloud. Day by day snapshots copied to immutable, off-site storage act as ransomware armor; if an attacker encrypts stay knowledge, a clear copy nonetheless waits in reserve underneath separate credentials.
Throughout diligence, ask three blunt questions:
- What are your documented RPO and RTO for payroll knowledge?
- The place are backups saved, and are they immutable?
- When was your final full-scale restoration check, and the way lengthy did it take?
Distributors who reply with exact numbers akin to “RPO 5 minutes, RTO three hours, final check handed on February 8” earn a spot in your shortlist. Those that hedge with “We’ve by no means wanted to” don’t.
7. Confirm certifications and the tradition behind them
Security measures stay or die by the workforce that builds and operates them. Impartial audits provide the quickest window into that tradition. Impartial, third-party attestations like SOC 2 and ISO 27001 are essential proxies for a vendor’s safety maturity. Nevertheless, knowledge from SaaS administration platform Vertice reveals important gaps within the software program provide chain: primarily based on its platform knowledge, solely 14% of SaaS distributors maintain a present SOC 2 report, 10% are ISO 27001 licensed, and simply 8% have each. Alarmingly, the identical report signifies that 19% of SaaS spending goes to distributors with no compliance certifications in any respect. This attestation hole presents a serious due diligence problem. Moreover, with the transition interval for the up to date ISO/IEC 27001:2022 normal ending on October 31, 2025, consumers should confirm that distributors are licensed in opposition to the present normal or have a transparent transition plan. If a payroll supplier can’t present a migration plan, the certificates might expire halfway via your contract.In case your group operates from a number of workplaces, exploring an ISO 27001 multi-site certification can consolidate these audits and slash the full value by roughly 40 %.
Deal with the dialog like a background test in your would-be associate in payroll knowledge safety software program:
- Ask for proof. A current SOC 2 Kind II letter underneath NDA and an ISO 27001 certificates dated 2024 or later are desk stakes.
- Hint the information path. The place will EU worker data stay, and might U.S. knowledge keep onshore? GDPR fines escalate when residency guarantees break.
- Comply with the chain. Which sub-processors deal with tax filings or financial institution payouts, and do they carry the identical certifications? The MOVEit supply-chain breach proved that one weak hyperlink can spill hundreds of thousands of pay data.
- Probe readiness. How briskly will the seller notify you of a breach? When did they final run a tabletop train? Practiced groups share playbooks; unprepared ones disguise behind legalese.
A supplier that solutions each level with dated paperwork, clear diagrams, and visual SLAs indicators a safety tradition you’ll be able to audit and belief. One which dodges or defers invitations you to turn out to be the subsequent cautionary story.
Regularly requested questions on payroll knowledge safety
What’s payroll knowledge safety software program?
It’s a specialised platform that secures payroll recordsdata and processes via encryption, role-based entry, audit logging, and different controls, guaranteeing workers are paid precisely whereas delicate knowledge stays non-public and compliant.
How does encryption shield payroll knowledge?
Encryption converts readable data into cipher textual content that may solely be unlocked with the right keys. If attackers intercept or exfiltrate encrypted payroll recordsdata, the information stays unreadable and due to this fact ineffective to them.
Which certifications ought to a payroll safety vendor have?
Search for an up-to-date SOC 2 Kind II report and an ISO 27001:2022 certificates at a minimal. Further attestations like ISO 27701 or FedRAMP can additional display a mature safety posture.
Wrapping it up
Payroll safety shouldn’t be a once-a-year audit; it’s an on a regular basis promise to the individuals who belief you with their most non-public particulars. We now have walked via the seven capabilities that flip that promise into follow:
- Position-based, least-privilege entry
- Obligatory multi-factor authentication
- Finish-to-end encryption in transit and at relaxation
- All the time-on audit trails with real-time alerts
- Fast, computerized safety updates
- Examined backups and quick catastrophe restoration
- Third-party-verified safety tradition and certifications
Deal with this listing as your scorecard whenever you consider payroll knowledge safety software program. After every demo, ask: Did the seller present each management working, and might they again every declare with contemporary proof? If the reply falls wanting all seven, preserve looking out.
Safety retains evolving, so construct for tomorrow in addition to at this time. Pair your chosen platform with compliance tooling or SIEM integrations that look ahead to drift between audits. Invite your IT and safety colleagues early; their questions will sharpen yours.
Select properly and also you achieve greater than compliance. You add confidence that individuals will likely be paid on time, each time, no matter tomorrow’s headlines. Your auditors transfer quicker, your board sleeps simpler, and your workforce sees an organization that guards what issues most.
Print the guidelines, preserve it the place you intend pay runs, and produce it to each assembly. Each paycheck, and each worker behind it, deserves the strongest lock you should purchase.